Cloud networking is complex and governed by numerous technologies, methodologies, and protocols.
One of the most fundamental protocols in cloud networking is tunneling.
What is network tunneling?
Tunneling is a method of discretely transmitting data across an otherwise public network. The transmission takes place using a public network; however, the data are intended for use only within a private network. Network tunnels provide a direct connection between a remote server and the local network, and the transmission of data is undetectable by the public network.
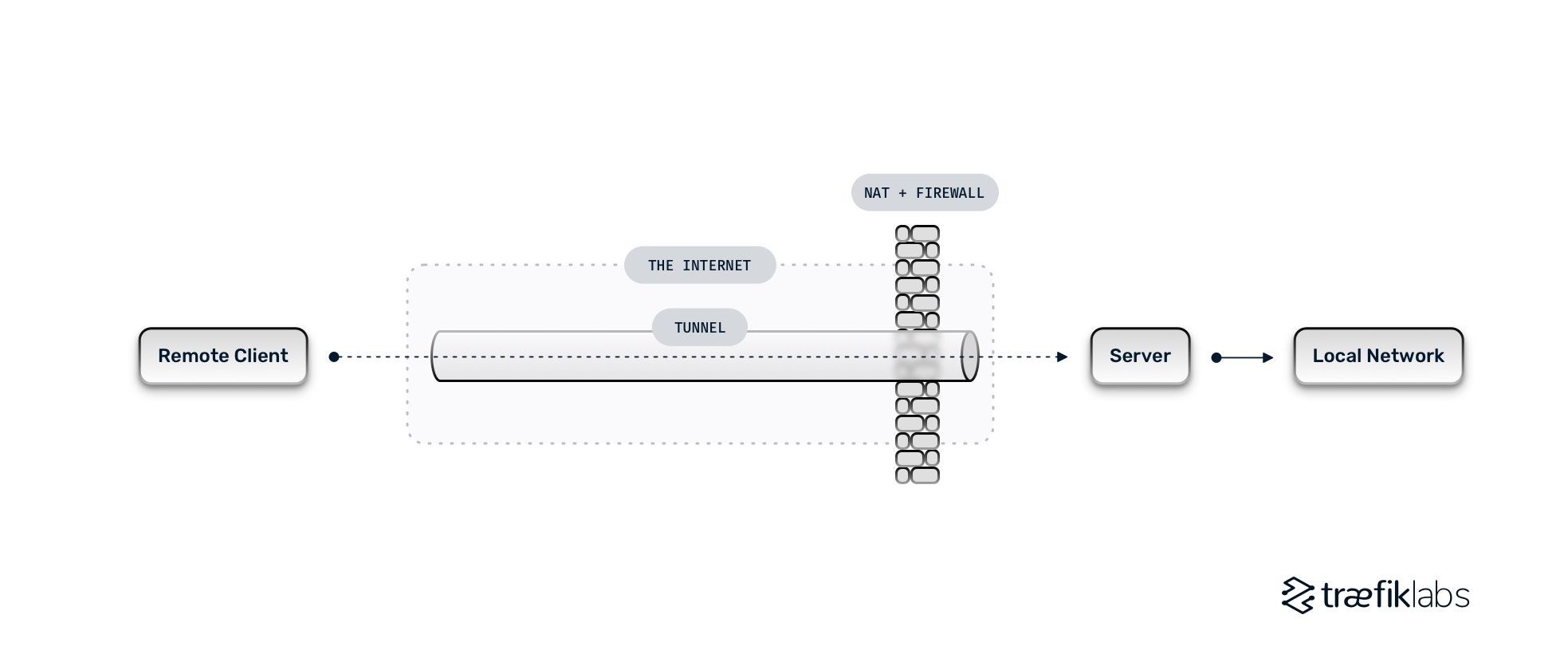
The most common use cases for network tunneling are virtual private networks (VPNs), which set up efficient and secure connections between networks, providing a way to overcome limitations when using unsupported network protocols, and allowing users to bypass firewalls.
How do network tunnels work?
In order to move requests through the tunnel from the remote client to the local network, requests need to be encapsulated. Network tunnels work using encapsulated packets of private network data and protocol information within the public network transmission. Those packets are then de-capsulated and decrypted at the final destination.
Packets usually consist of two parts: the header, which indicates the packet's destination and the protocol it uses, and the payload, which includes the packet's contents. An encapsulated packet is a packet wrapped inside another packet as the payload.
What is a VPN tunnel?
A VPN tunnel is a connection between your machine and a VPN server. A VPN tunnel connects your device to a server from a different network and allows them to communicate as if they were part of the same network. VPNs tunnels can also be used to protect users from attacks and hide their online activity.
Split tunneling vs. full tunneling
Split tunneling allows some applications to use a secure VPN tunnel, while others that require better performance are transmitted directly outside the tunnel.
Full tunneling means that all traffic goes through a secure VPN tunnel. This is, by default, the most secure option, but it has an impact on performance and speed since the entire traffic is encrypted.
What is a Secure Shell (SSH) tunnel?
Secure Shell (SSH) tunneling is a method for transmitting network data using the Secure Socket Shell (SSH) communication protocol. It can be used to add encryption to legacy applications. It can also be used to implement VPNs (Virtual Private Networks) and access intranet services across firewalls.
SSH tunneling is the standard for securing remote logins and file transfers when using untrusted networks. The most common use cases for SSH tunnels are encrypting legacy applications, creating VPNs, and accessing intranet services by bypassing firewalls.
Why should you use tunneling?
The main benefit of using network tunnels is that it simplifies communication by avoiding configuration steps. Tunnels allow you to connect two elements within a complex network, avoiding firewalls, and other configuration steps. For example, in order to communicate between your local machine and a server within your company network without a tunnel, you need to create a connection that will go through your internet connection, then through a series of servers until it reaches the final destination. Using a tunnel, you directly connect point A (your machine) to point B (the local network), bypassing all intermediate steps.
Potential drawbacks
Speed: Due to the process of encapsulation, tunneling can make communication a bit slower.
Security: Because tunnels are designed to skip firewalls, tunneling opens a door directly to your local network. The responsibility of securing the tunnel falls to the person that creates the tunnel. For this reason, some organizations block the creation of tunnels altogether.
💡 Note: The way to secure a tunnel is by encrypting the data between the remote client and the server allowing only the specific client and server that are connected through the tunnel to decrypt the data. Using an SSH tunnel, the request is encrypted, and the receiving server is the only one that has the key to decrypt the data within the request.
Protocols used in network tunneling
Network tunnels depend on the communication protocols that are used to encapsulate and transmit the data.
Point-to-Point Tunneling Protocol (PPTP): a network protocol that enables data transfer from a remote client to a private network. PPTP creates a VPN, operating on TCP port 1723. PPTP is one of the oldest VPN protocols, and it supports on-demand and multi-protocol VPNs. Although PPTP is fast and easy to set up, it is inherently insecure — mostly due to security vulnerabilities related to its underlying authentication protocols — and it is not recommended for use in any environments where security is essential.
Secure Socket Tunneling Protocol (SSTP): a protocol commonly used in VPNs that limits traffic over HyperText Transfer Protocol Secure (HTTPS), and enables VPN traffic to bypass most firewalls. SSTP was developed by Microsoft, and it’s most commonly used in Windows environments.
Layer 2 Tunneling Protocol (L2TP): an extension of the PPTP that is commonly used by internet service providers to enable VPNs. L2TP is not secure out of the box, and for this reason, it needs to rely on an encryption protocol. L2TP is a session layer protocol (based on the OSI model), and it is used to transmit Layer Two (L2) data types over an IP or Layer Three (L3) network.
Virtual Extensible Local Area Network (VXLAN): an encapsulation protocol that uses tunnels to run overlay networks on existing L3 infrastructures. VXLAN is commonly used by network engineers to scale cloud computing environments while maintaining the isolation of apps and tenants.
Generic Routing Encapsulation (GRE): an encapsulation protocol that uses a virtual point-to-point link. GRE is defined in RFC2784 and is supported by all vendors. It also supports multicast packets and can be used with dynamic routing protocols. However, it does not have any built-in encryption protocols.
IP-in-IP: a low-level tunneling protocol that encapsulates an IP packet within another IP packet to connect two IP networks. When using IP-in-IP encapsulations, the outer header of the IP packet includes the Source IP that acts as the entry point of the tunnel, while the Destination IP is the exit point. IP-in-IP is defined in RFC1853.
Network tunneling in action
Complicated protocols aside, the simplest way to start using tunneling in application development is by publishing and securing your services with Traefik Hub.
Tunneling enables a variety of use cases, and that is why we use tunneling inside Traefik Hub. Traefik Hub removes all the complex configuration work required to set up a tunnel. The agent just spins up a secure tunnel to our cloud-based platform. That tunnel then is used to publish services running alongside the agent, simple, secure, and fully automated to the edge. By utilizing a tunnel, it’s possible to overcome well-known networking challenges, such as NAT, in networking constraint environments.
Watch the video below for a detailed walkthrough of Traefik Hub. If you’re ready to try it out yourself, sign up for free today.